Enabling Burp Suite Proxy on Linux
03/08/2020
The Burp Suite proxy is a powerful tool for security researchers. It allows users to intercept and examine network traffics with efficiency.
Intercepting unencrypted HTTP traffics is straightforward by setting the proxy. But doing the same thing on HTTPS traffics requires extra steps since HTTPS is designed to prevent unauthorized interceptions. To intercept HTTPS traffic, the user must authorize the use of Burp Suite proxy by installing the provided Burp Suite CA certificate onto the target system.
Here are the basic steps needed to enable Burp Suite proxy on a target Linux system:
Certificate Export and Installation
Open Burp Suite. Export certificate from Burp in DER format in “Proxy” -> “Options”.
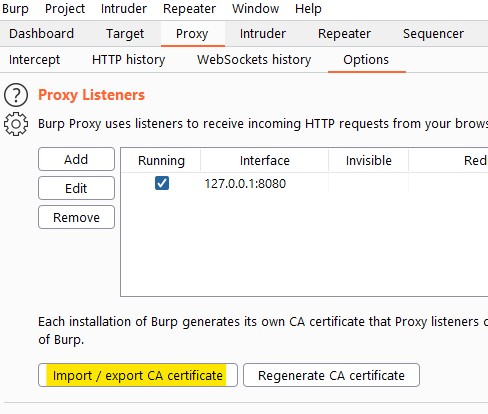
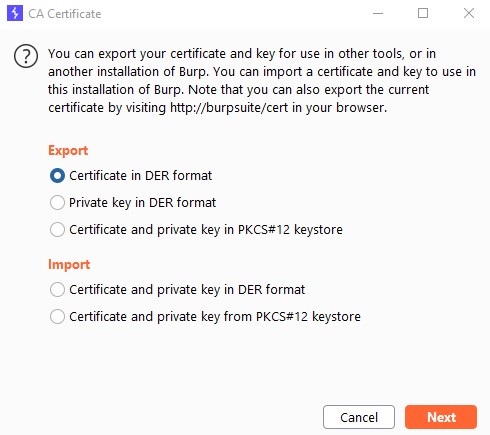
Copy the DER certificate to target Linux system.
Convert certificate from DER to PEM with openssl tool:
openssl x509 -in [cert.der] -inform der -out [cert.crt] -outform pem
Copy the PEM certificate to /usr/local/share/ca-certificates/
Update the CA store by running
sudo update-ca-certificates
The certificate should be imported into /etc/ssl/certs/ and accepted as a valid CA certificate.
Setting Up Proxy
Use export commands to set up the proxy.
export http_proxy="address:port"
export https_proxy="address:port"
export no_proxy="localhost,127.0.0.1"
To make it permanent for all users, open /etc/environment with text editor and add the statements above to the file.